Explain briefly the meaning of each of the following terms giving examples where necessary.
(a)Automation
(b)HTML
(c) DBMS
(d) Data How Diagrams (DFD)
(e) Data protection
(15 marks)
How does the Data .Protection Act define the following terms?
(a) Data
(b) Data subject
(c) Personal data
(5 marks)
2)
(a) What is teleworking?
b) List two advantages of teleworking to a teacher,
(c) List and describe two advantages, of teleworking to a school.
(ii) Below is a diagram of the structure of a typical network topology.$
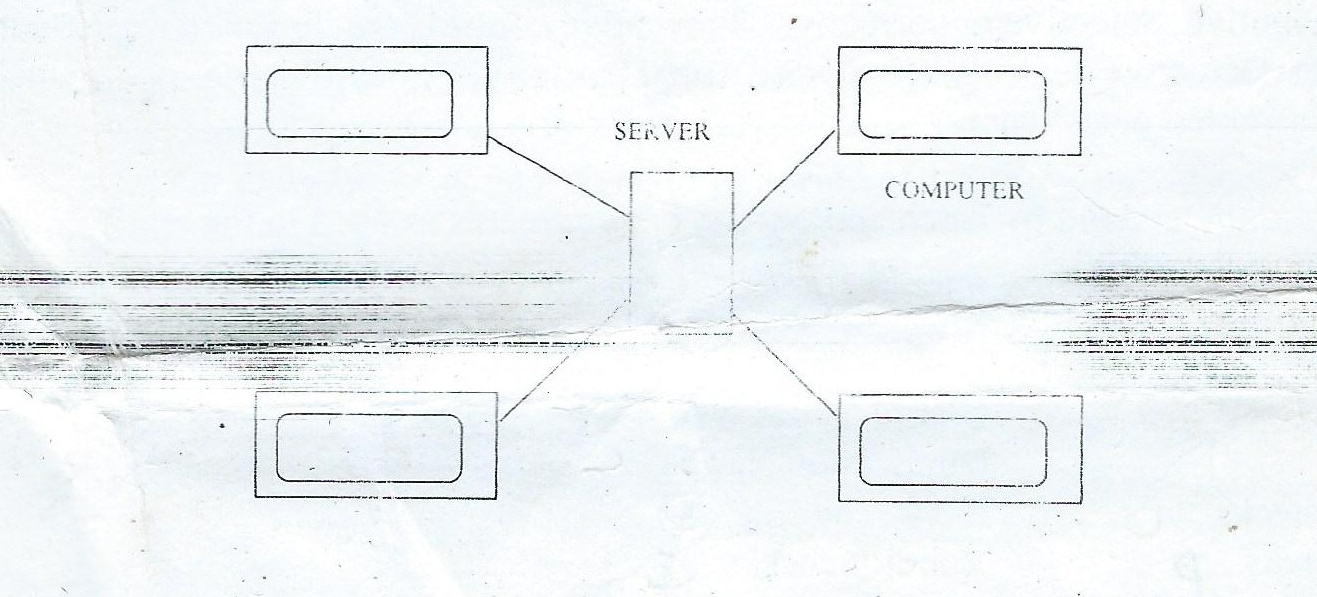
(a)Give the name of the network topology. above. Give the name cf another typical network topology.
(2 marks)
(b) Give two reasons why it is better for students to use networked computers. (4 marks)
(c) List two functions of a file server on the network,, (2 marks)
(d) .The school has an intranet which students can log on to from home through a WAN, (2 marks)
(i) Explain the meaning of WAN.
(ii) List two different ways in which the intr,Inct can help students in their studies. (2marks)
3)
(a) What is ergonomics? (2 marks)
(b) List and explain-three physical health matters related to the use of computers.
Give possible ways of avoiding each of these problems. (6 marks)
(ii) (a) Explain the use and functioning of the following:
– Bar code readers
Optical Mark Recognition (OMR)
(b) List two main finctions of each of the following hardware:
– Video card
-Sound card
-NIC
4)
(i) (a) Explain the meaning of the term “data security”
(b) List and explain TWO main threats to the safety of data and used to fight against it.
(c)Describe how encryption will help to protect information or a message which is sent across a network
(ii)
(a) Explain how each_of the following methods could be used
-Parallel running
-Direct changeover
-Phased implementation
(b) Give one advantage and one disadvantage of each of the methods in (ii)a
(4 marks)
Read the text below and answer the questions that following
APPLICATION CON’TOL STANDARDS (ACS)
ACS includes policies and procedures associated with uses activities and the auto4ed controls designed into applications. Controls could be in place to address both batch and on-line environments.
ACS enhances the security, integrity, and reliability of automated systems by ensuring that input, processed and output information are authorised, accurate, complete and secure. Management considers these issues at the outset of a project and includes them as soon as possible in applications and systems design. Controls are usually categorised as preventive, detective or corrective. Preventive controls are designed to prevent unauthorised or invalid data entries. Detective controls help identify unauthorised or invalid entries. Corrective controls assist in recovering from unwanted occurrences.
(i) What do understand by batch and on-line environments as used in the text?
(ii) Give the purpose of automated input control in (i)
(ii) group the following detective and their corrective control
_
Check digits Completeness check
Range checks Duplication checks
Format Checks Error reporting
Limit Check Validity checks
(8 marks)
(ii) Explain how you will implement format and range checks in a spreadsheet . Use examples from: Name, Sex, Date and Marks fields.
(5 marks)
6)
a)Explain the meaning of the term “expert system”
Give toy situation where expert systems are used other than in playing the game of chess
b) Describe now a user interacts with an expert system.
(i)Name four computer crimes common in Cameroon today and briefly describe each of them.
(4 marks)
(ii) for any two of the crimes you named above state for each, two -ways.that you can use to prevent thee;
(4 marks)
•
.
(iii) state and explain two reasons why a data protection law is necessary in Cameroon. (4 marks)
Briefly describe what the following computer professionals do:
(a) Database Administrator
(b) Systems Analyst
(c) Computer .programing
(d) Networks System Administrator
(8 mark)
8. (i) High level languages are machine independent while low level languages are machine oriented.
•
(a) Give one example of a high level language
(b) Explain the meaning of the following two terms:.
Machine independent
Machine oriented
( c) Low level and high level languages are different. List three features of each language
level that is not found in the Other.
In a given firm the wages of workers are calculated as follows:
Wages depend on hours worked and pay rate (amount per hour). Wages for extra hours greater than 40 have rate of 1.5 times pay rate. (1 mark)
(3 marks)
(6 marks)
(i) write an algorithm that receive the number of hours worked and pay the rate as input and the calculated the wages
e
(ii) Use your algorithm to calculate a worker wages who worked for 43 hours at a pay rate of 1000frs
9)
i) Distinguish between Network topology and Network configuration. (2 marks)
(ii) Name and describe two types of Network configurations . (4 marks)
(iii) You were asked to design computer networks in different geographical areas. Choose what type o network you .would design for the ones below.
(a) A network to link a laptop, a desktop, a digital camera and a PDA in a corner of a room.
(b) A network all the networks of a multinational company’s offices in two continents.
(c) A network to link computers of a company’s in one large city.
(d) A network to link all computers in many buildings of a college inside a fence. (4 marks)
(iv) convert from 2 to decimal toe number 101101.01011. Convert the decimal number 268 to octal.
convert the binary number 110101101110 to octal.
(v)
Design and complete the truth table of the following logic operators NOR and AND
(vi) an Operating System (OS) Give two functions of an operating system. (4 marks)
(2 marks) (4 mark)














